


Is your business prepared for the next cyber threat?
Secure your business with Resilient Cybersecurity solutions
designed for small and mid- sized businesses. As your trusted
partner, we deliver innovative, risk-intelligent protection against
financial losses, reputational damage, and loss of customer trust.
Why should I choose your cybersecurity services?
We offer complimentary security assessments that provide
valuable insights into your current cybersecurity posture.
Our experts then utilize this knowledge to develop a customized
defense strategy, implementing best-in-class security solutions.
This approach fortifies your defenses against evolving cyber
threats, ensuring robust protection for your organization.
How do we protect against cyber threats?
We equip your workforce with extensive training to become
cyber threat experts. They gain invaluable skills to proactively
identify and neutralize industry-specific cyber risks.
Our multi-layered defense strategy integrates stringent access
controls, military-grade encryption, continuous employee
education, and advanced security measures. This impenetrable
fortification ensures watertight protection for your organization's
mission-critical data and assets.
Security Challenges

Cybersecurity breaches can lead to significant financial losses, reputational damage, and loss of customer trust.
The average total cost of a data breach reached $4.35 million in 2022, a 2.6% increase from the prior year.
Non-compliance with regulatory mandates like the SEC cyber disclosure rule can result in penalties, legal action, and damage to the company's reputation.
The SEC's proposed rules would require public companies to disclose material cybersecurity incidents and periodically provide updates about previously reported incidents.
Cybersecurity solutions can be expensive, and many small to medium-sized businesses struggle to allocate sufficient resources to protect their assets.
66% of small and medium-sized businesses reported that their cybersecurity budget is insufficient to meet their needs.
How can Periscope help?

Fortifying Your Defenses Against Cyber Threats
With our extensive experience in cybersecurity and software architecture best practices, we enable seamless integration of risk-intelligent solutions into your enterprise systems. Making the complex simple.
Ensuring Compliance and Safeguarding Your Reputation
Comprehensive, made-to-measure Risk & Compliance solutions that adapt to your evolving requirements.

Optimizing Your Cybersecurity Spend
Cost-effective, accessible cybersecurity solutions tailored for small to medium-sized public and private companies facing budget and talent constraints.
What's Our Approach?
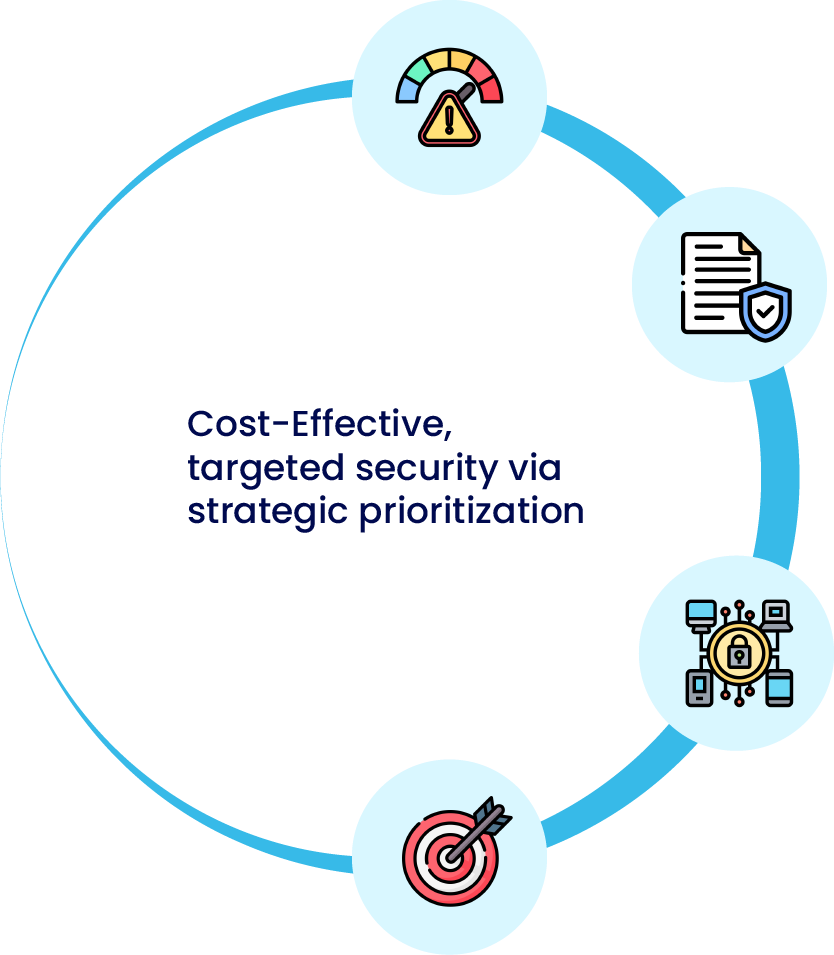
Cost-Effective target security via strategic prioritization.

Prioritize top security threats with risk management program.

Create security policies for compliance & IP protection.

Implement baseline security solutions.

Align cybersecurity initiatives with business goals.

Align cybersecurity initiatives with business goals.
Prioritize top security threats with
risk management program.
Create security policies for
compliance & IP protection.
Implement baseline
security solutions.
Align cybersecurity initiatives with
business goals.
Periscope Cybersecurity Implementation Methodology
Curious about our Framework-Driven Implementation Strategy?
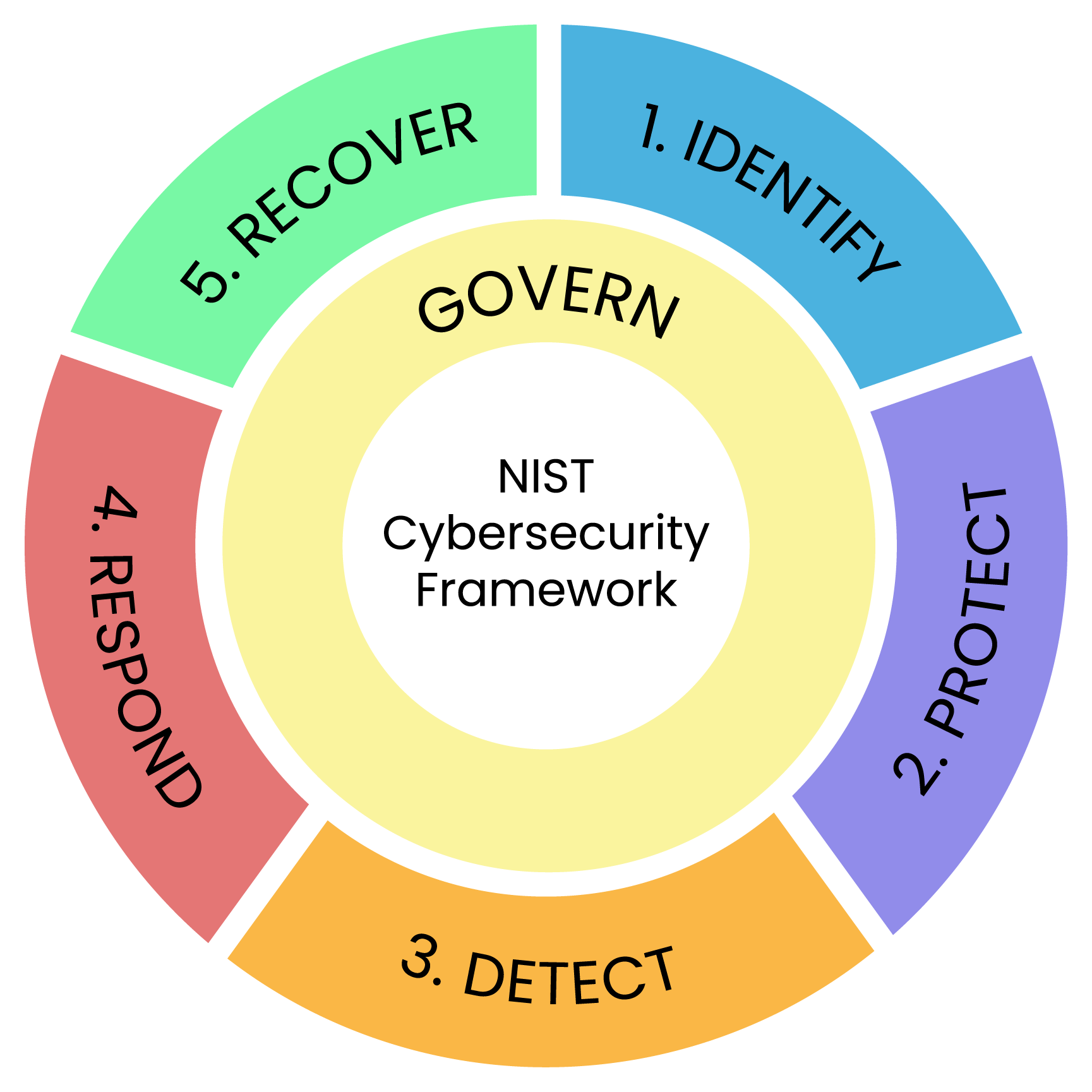
Let's Dive into Our NIST CSF-Aligned Approach
NIST Cybersecurity Risk Management Assessment
Framework used
NIST Cybersecurity Framework (CSF).

Results
Quantitative assessment across 5 areas, 23 categories, and 108 subcategories.

Top 5 Critical Security Risks
- Detection Inadequacy: Inadequate abilities to detect and report cyber threats and incidents.
- Data Exposure: Significant risk of theft or exposure of highly confidential data.
- Insider Threats: Risks posed by malicious or negligent insiders with access to sensitive data and systems.
- Weak Access Controls: Insufficient or poorly implemented access controls, increasing the risk of unauthorized access.
- Advanced Persistence: Advanced persistent threats from sophisticated actors targeting long-term data exfiltration.

Outcome
Identified critical risks and directed remediation plan. Gaps in 'N' out of 23 categories.
Framework used
NIST Cybersecurity Framework (CSF)
Top 5 Critical Security Risks
- Detection Inadequacy: Inadequate abilities to detect and report cyber threats and incidents.
- Data Exposure: Significant risk of theft or exposure of highly confidential data.
- Insider Threats: Risks posed by malicious or negligent insiders with access to sensitive data and systems.
- Weak Access Controls: Insufficient or poorly implemented access controls, increasing the risk of unauthorized access.
- Advanced Persistence: Advanced persistent threats from sophisticated actors targeting long-term data exfiltration.

Results
Quantitative assessment across 5 areas, 23 categories, and 108 subcategories

Outcome
Identified critical risks and directed remediation plan. Gaps in 'N' out of 23 categories
NIST CSF Security Assessment Deliverables
The policy and practice score in the table describes the current maturity level of each NIST CSF category.
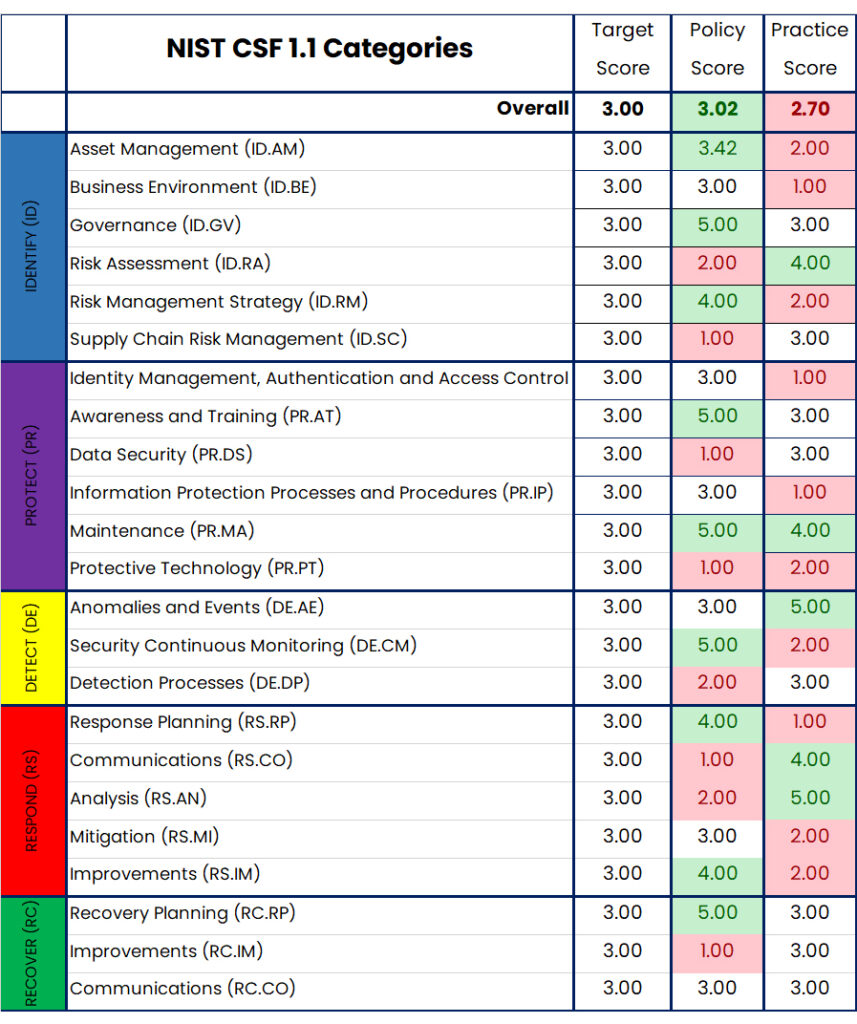
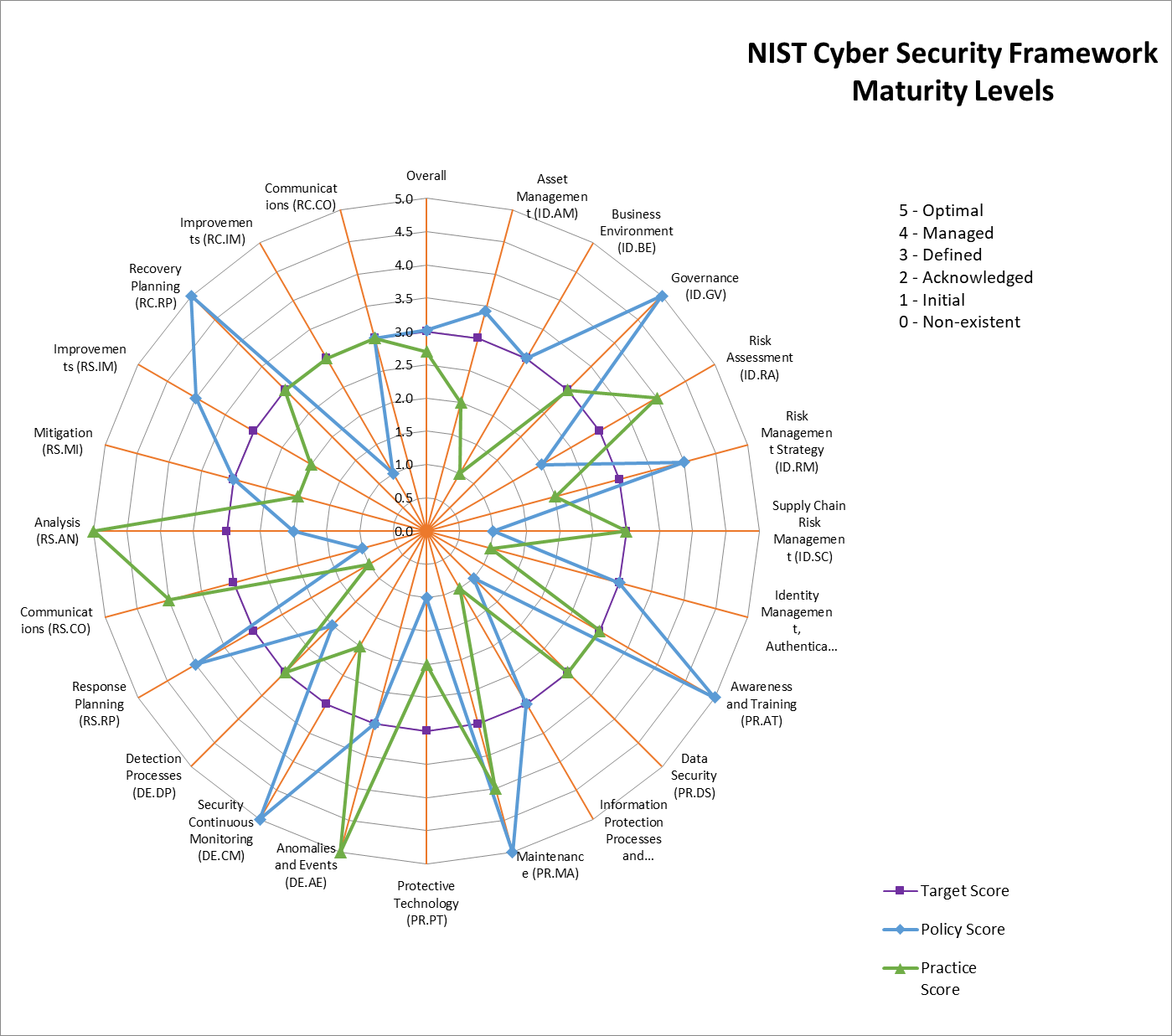
The radar chart below provides a graphical summary of the assessment outcome.
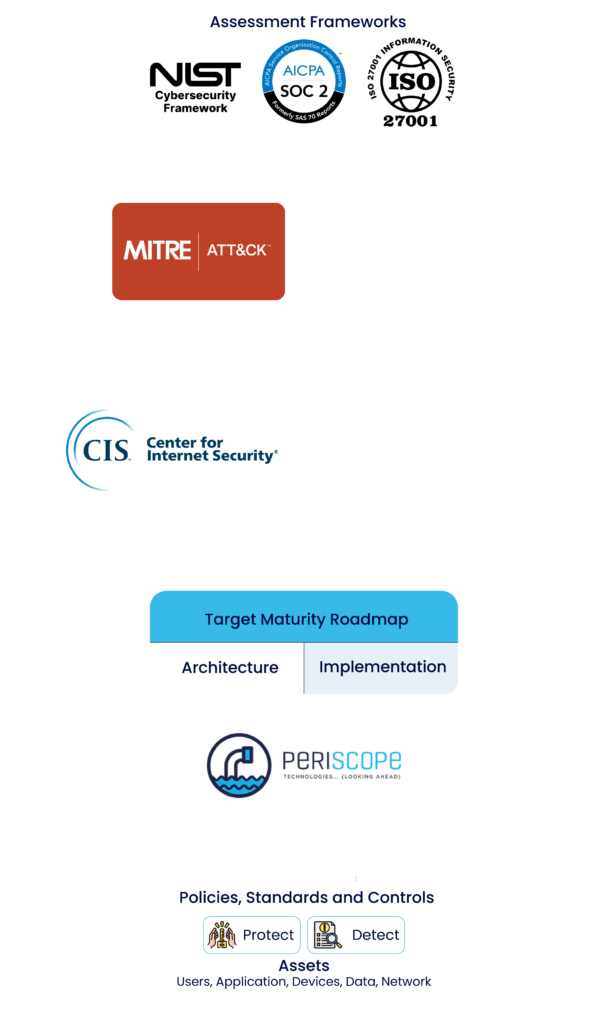
Assessment to Target Maturity Roadmap to Implementation

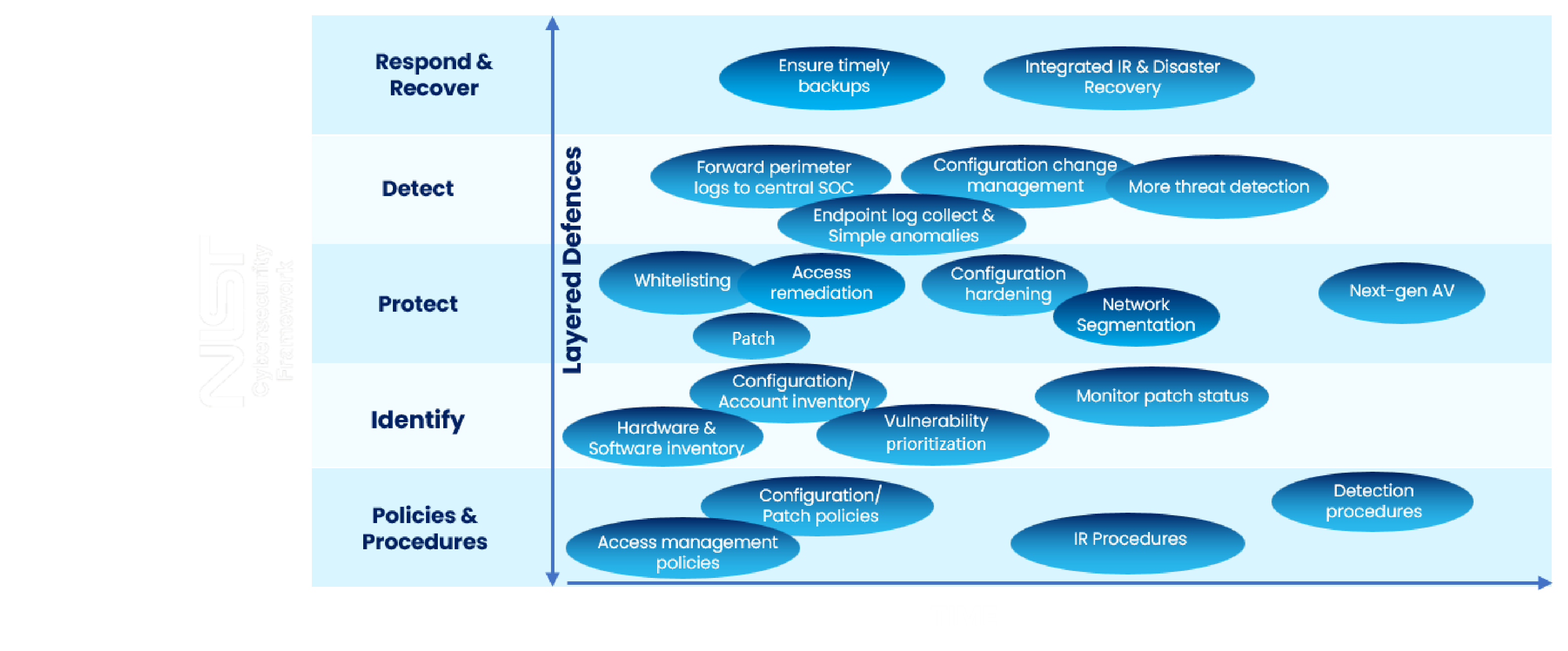
A TMR outlines a phased approach to establish, enhance and optimize
an organizations cybersecurity posture and controls over time
Building Your Cyber Roadmap

Address top security threats.

Focus on building a core risk management program & roadmap.

Organization security policy to mitigate #1 compliance risk and #2 IP theft protection.

Deploy minimum viable solutions to establish a base set of cybersecurity policies and infrastructure to begin maturation initiatives aligned with the organization's business goals.

CyberSecurity Services

Network Detection and Response (NDR)
Protect your growing hybrid networks with our NDR solution powered by WatchGuard ThreatSync+ . Our managed service offers full visibility across both on-premise and cloud environments, detecting and responding to threats in real-time while ensuring continuous compliance. With 24/7 expert monitoring, configuration, and reporting, we eliminate the need for an in-house SOC, keeping your security optimized and worry-free.
Internal Network Detection & Response (INDR)
Protect your growing hybrid networks with our NDR solution powered by WatchGuard ThreatSync+ . Our managed service offers full visibility across both on-premise and cloud environments, detecting and responding to threats in real-time while ensuring continuous compliance. With 24/7 expert monitoring, configuration, and reporting, we eliminate the need for an in-house SOC, keeping your security optimized and worry-free.

External Security Monitoring (ESM)
Secure your expanding digital footprint with our comprehensive ESM solution powered by Periscope, providing continuous visibility across cloud assets and third-party services while detecting threats in real-time. With automated discovery and 24/7 expert monitoring, we eliminate the need for specialized security staff, keeping your external attack surface protected.

Identity Access Management
Don't let weak identity management expose your data. Our expert team implements robust Identity Management solutions, leveraging tools like Microsoft Entra and Multi-Factor Authentication. We streamline user access, enforce granular controls, and empower you to take control of your organization's security posture. Let us help you build a digital fortress and achieve peace of mind.

Network Detection and Response (NDR)
Protect your growing hybrid networks with our NDR solution powered by WatchGuard ThreatSync+ . Our managed service offers full visibility across both on-premise and cloud environments, detecting and responding to threats in real-time while ensuring continuous compliance. With 24/7 expert monitoring, configuration, and reporting, we eliminate the need for an in-house SOC, keeping your security optimized and worry-free.
Industries
See how Periscope can protect your critical data and avoid costly data breaches

Our Clients




































