


Is your remote workforce truly secure?
Employees connect from home, cafés, airports, and hotel Wi-Fi often on personal devices. One infected laptop, phone, or compromised password could silently leak sensitive data or give attackers access to your entire network. Most companies don’t even realize how exposed they are until it’s too late.
Could your business survive the next cyberattack?
Attackers don’t announce themselves. AI-generated phishing, stolen credentials, and insider mistakes can silently compromise your systems. One small oversight today can become a full-blown crisis tomorrow.
How quickly would you notice a phishing attack or insider breach?
Minutes, hours, or days? Most companies only find out after damage is done data stolen, systems compromised, operations disrupted. AI watches every endpoint and login 24/7, flagging suspicious activity in real time. Without it, threats can quietly spread before anyone even notices.
The 2026 Threat Matrix
Credential & Identity Theft
The Risk: Sophisticated phishing and identity spoofing.
The Defense: MFA & AuthPoint. We implement biometric-backed identity gates that stop unauthorized access at the point of entry
Fileless & Zero-Day Malware
The Risk: Stealthy attacks that bypass traditional antivirus.
The Defense: AI-Driven EPDR. Our system uses behavioral analysis to detect and block unknown scripts in milliseconds.
Hidden Infrastructure Gaps
The Risk: Blind spots in complex systems that automated tools overlook.
The Defense: Managed Detection (MDR). Our team performs continuous threat hunting to identify and neutralize what automated software misses
Unsecured Remote Access
The Risk: Outdated VPNs acting as open doors for hackers.
The Defense: Zero Trust (ZTNA). We replace legacy VPNs with identity-verified tunnels, granting secure access only to authorized users on any network.
Why Periscope
Periscope Technologies Inc. is a software and IT powerhouse that builds security into the DNA of your cloud and code. We provide the structural foundation of IT and the shield of Cybersecurity in one unified stack, ensuring your digital assets are resilient by design.
Our Core Pillars
- Hardened Cloud Migration: Move to the cloud with Zero Trust pre-installed.
- Secure Software Dev: Enterprise-grade code audited for vulnerabilities from Day 1.
- Managed IT Resilience: Proactive helpdesk support backed by security engineers.
We focus on rapid execution, delivery, and support for high-stakes industries, including FinTech, InsurTech, Law Enforcement, Aviation, Construction, and EdTech. At Periscope, we don’t just fix IT we engineer the secure architecture your business deserves.
Discover Today’s Cyber Exposure Risks - Free Report

Are You Truly Secure, or Just Lucky?
-
In December 2025, the "perimeter" of your business has dissolved. It is no longer a server room you can lock; it is a thousand invisible entry points. Attackers are now using Agentic AI Swarms autonomous digital entities that don't just "hack," they reconnaissance, socially engineer, and exfiltrate at machine speed.
Remote work broke old security assumptions. Employees connect from home, cafés, airports, and hotel Wi-Fi often using personal devices. One infected laptop or phone can expose sensitive data or open silent backdoors.
If you are relying on a firewall era and an overstretched IT team, you aren't just behind you are invisible to your own data.
Our Clients












The Invisible Risks
How We Secure Your Business and Close Every Security Gap

- Detect threats in minutes.
- AI-driven visibility across endpoints, cloud, and identities detects lateral movement early and automatically contains attacks before impact.
- Faster Detection, Visibility & Reduced Exposure

- Secure every device, users and apps
- Continuous behavioral monitoring protects remote and unmanaged devices, isolating risky activity at the edge before it reach to the systems.
- Reduced remote attack risk and safer hybrid work.

- Stop AI attacks with AI speed.
- AI correlates weak signals across your environment to predict, detect, and stop threats automatically 24/7.
- Continuous protection with automated response.

- Zero Trust: Verify Every Login
- Access is continuously validated using user and device intelligence, blocking abnormal login behavior in real time.
- Stronger control, lower credential risk
- Prevent silent cloud data leaks.
- Real-time monitoring detects risky configurations and auto-remediates cloud exposure across active and unused resources.
- Lower cloud risk and improved compliance.

- Spot risky behaviour before it becomes a breach.
- AI continuously monitors user behavior, flags anomalies, and isolates insider threats before data is compromised.
- Reduced insider risk, faster threat response.
Real Time Attack Surface Monitoring
- Detect threats in minutes.
- AI-driven visibility across endpoints, cloud, and identities detects lateral movement early and automatically contains attacks before impact.
- Faster Detection, Visibility & Reduced Exposure
Remote Workforce Protection
- Secure every device, users and apps
- Continuous behavioral monitoring protects remote and unmanaged devices, isolating risky activity at the edge before it reach to the systems.
- Reduced remote attack risk and safer hybrid work.
24/7 Autonomous AI Defense
- Stop AI attacks with AI speed.
- AI correlates weak signals across your environment to predict, detect, and stop threats automatically 24/7.
- Continuous protection with automated response.
Identity & Access Control
- Zero Trust: Verify Every Login
- Access is continuously validated using user and device intelligence, blocking abnormal login behavior in real time.
- Stronger control, lower credential risk
Cloud & Infrastructure Resilience
- Prevent silent cloud data leaks.
- Real-time monitoring detects risky configurations and auto-remediates cloud exposure across active and unused resources.
- Lower cloud risk and improved compliance.
Insider Risk & Behavioral Monitoring
- Spot risky behaviour before it becomes a breach.
- AI continuously monitors user behavior, flags anomalies, and isolates insider threats before data is compromised.
- Reduced insider risk, faster threat response.
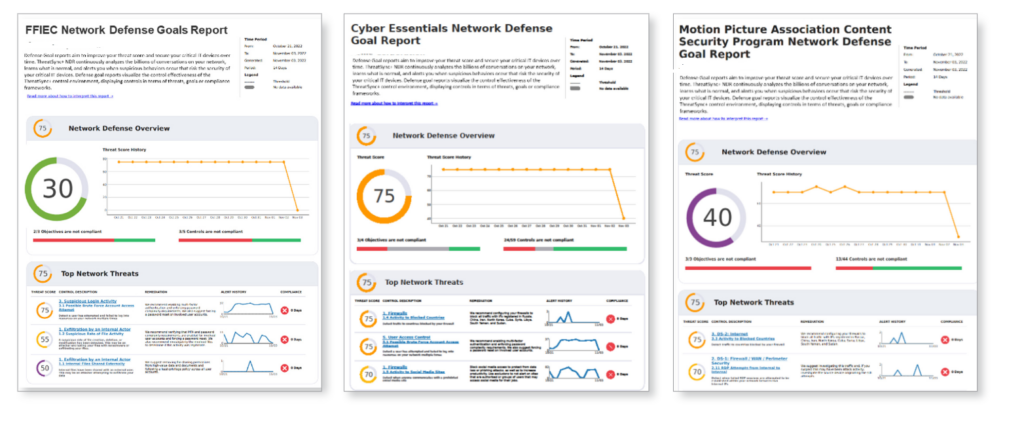
Sample Periscope Exposure Audit Reports
What the Report Includes
- Endpoint Vulnerability Map: Which remote devices are leaking data.
- Zero-Day Readiness Score: How your current stack handles unknown threats.
- MFA Compliance Check: Identifying accounts without AuthPoint protection.
- Shadow IT Audit: Detection of unauthorized AI tools and software on your network.
Case Studies
Testimonials
Periscope didn't just give us tools; they gave us sight. They closed compliance gaps we didn't know existed.
Executive FAQs
1. Why Periscope instead of a standard audit?
Audits only show you what went wrong in the past. Periscope is a live scan of the future. We find the hidden risks like “Identity Drift” and rogue AI that a static checklist will always miss.
2. How does this solve our IT staffing shortage?
You get a full security team without the hiring headaches. Our Total MDR service provides 24/7 monitoring. Our AI and human experts watch your network while you sleep, so your team doesn’t have to.
3. We have "strong tools" already. Why do we need you?
Most tools work in isolation, creating Blind Spots. In 2025, most companies that got hacked already had “strong tools.” Periscope connects everything, spotting attackers who try to hide in the gaps between your systems.
4. What is "Identity Drift" and why should I care?
It’s when a user’s access level slowly changes or stays active when it shouldn’t. It’s the #1 way hackers move through a company. We use Mobile DNA to make sure the person logging in is actually who they say they are.
5. Can you actually stop an attack at 3:00 AM?
Yes. Our AI doesn’t wait for a human to wake up. It detects “machine-speed” threats like ransomware and automatically freezes the infected device before the virus can spread to the rest of your company.



